Contact Expert v7.6
Contact Expert Prerequisites
Introduction
This article describes the hardware, software and configuration prerequisites that need to be set up for a successful Contact Expert implementation via the following specific Scaled Implementation Scenarios:
Servers:
- CE Database Host for running Microsoft SQL Server and hosting Contact Expert databases;
- CE Core Host for running Contact Expert core services;
- CE Recorder Host for running Contact Expert call recording services;
Client PCs:
- CE Administrator PC for running CE administrative tools;
- CE Operator PC for running agent (operator) application and Microsoft Skype for Business client software in Skype for Business environment.
To learn more about the sizing of the deployment, please read the Deployment sizing section.
Minimum Hardware and Software Requirements
The following tables show the minimum requirements.
Note
These capacity figures must be available for Contact Expert software components. In case additional 3rd party software is planned to be co-located with any server or agent CE component, then these figures need to be increased accordingly.
CE Server Components
| Resource | CE Core Host | CE Database Host | CE Recorder Host (9) |
|---|---|---|---|
| CPU | Intel Xeon 2 GHz (15) | Intel Xeon 2 GHz (15) | Intel Xeon 2 GHz (15) |
| Architecture | x64 | x64 | x64 |
| RAM | 4 GB | 4 GB | |
| Storage | 40 GB | 40 GB | |
| Network | 100 MBit/sec | 100 MBit/sec | |
| OS | Microsoft Windows Server 2012 R2 / 2016 / 2019 / 2022 (1) | Microsoft Windows Server 2012 R2 / 2016 / 2019 / 2022 (1) | Microsoft Windows Server 2012 R2 / 2016 / 2019 / 2022 (1) |
| Software | Microsoft Windows Server Roles and Features as listed in this article below Google Chrome, Microsoft Chromium Edge, Microsoft Internet Explorer 11 or above (13) Microsoft UCMA 4.0 / 5.0 Runtime (5)(6) At least one Microsoft Speech TTS language pack (5)(7) Microsoft .NET Framework 4.8 Microsoft ASP.NET Core Hosting Bundle 6.0.20 or newer (18) Microsoft Visual C++ 2017 Redistributable Update 4 x86 (16)(8) Microsoft Visual C++ 2017 Redistributable Update 4 x64 (16)(8) Java JDK 17 Windows X64 (5)(12) Avaya TSAPI Runtime 3.1 (5)(11) |
Microsoft SQL Server 2012 / 2014 / 2016 / 2017 / 2019 (2) collation: SQL_Latin1_General_CP1_CI_AS |
Microsoft Windows Server Roles and Features as listed in this article below Google Chrome, Microsoft Chromium Edge, Microsoft Internet Explorer 11 or above (13) |
| Virtualization | Microsoft Hyper-V, VMware vSphere | Microsoft Hyper-V, VMware vSphere | Microsoft Hyper-V, VMware vSphere |
CE Client & Admin Components
| Resource | Administrator PC | Agent PC |
|---|---|---|
| CPU | Intel Core iX 2 GHz with at least 2 cores | Intel Core iX 2 GHz with at least 2 cores |
| Architecture | x86 or x64 | x86 or x64 |
| RAM | 4 GB | 4 GB |
| Storage | 100 GB | 80 GB |
| Network | 100 MBit/sec | 100 MBit/sec |
| OS | Microsoft Windows 10 / 11 (1) | Microsoft Windows 10 / 11 (1) |
| Software | Google Chrome, Microsoft Chromium Edge | Google Chrome, Microsoft Chromium Edge, Microsoft Internet Explorer 11 or above (13) Microsoft Lync 2013 / Skype for Business 2015 / Skype for Business 2016 client (10) Microsoft .NET Framework 4.8 x64 mandatory for Scripting (17) Microsoft .NET Framework 4.8 x86 for 32-bit OS Microsoft Visual C++ 2017 Redistributable x86 |
| Virtualization | Microsoft Hyper-V, VMware vSphere | Microsoft Hyper-V, VMware vSphere |
Notes
| (1) | Latest service packs and security updates are recommended to be installed on a continuous basis. English GUI is preferred. |
| (2) | Latest service packs are recommended to be installed. Both Standard and Enterprise Edition are supported. Mixed Authentication Mode must be enabled. Microsoft SQL Server Management Studio component is required. |
| (3) | Server with a GUI option is required when installing Windows Server 2012 R2. Do not use Server Core Installation option. When using Windows Server 2016 or above, the Desktop Experience edition is required. |
| (4) | All sub-roles/sub-features are required. Please make sure that all sub-roles/-sub-features are selected when adding the role or feature. |
| (5) | The setup file is available on the Contact Expert installation media (DVD or ISO image). |
| (6) | Bear in mind that UCMA 4.0 / 5.0 must be synchronized with the latest Microsoft Lync Server 2013 / Skype for Business Server 2015 Cumulative Update version applied on your Lync / Skype for Business Front End Server(s). In case of FreePBX platform, install UCMA 5.0, it is required for TTS. |
| (7) | Installing the en-US language pack (MSSpeech_TTS_en-US_Helen.msi) is required even if you install additional language packs; other language packs are optional. |
| (8) | Both x86 and x64 versions are required. |
| (9) | For ~80 agents, see Deployment sizing for further details. |
| (10) | Required for Contact Expert for Microsoft Lync / Skype for Business only. |
| (11) | Required for Contact Expert for Avaya Communication Manager only. |
| (12) | This is the only supported Java version. No other version is supported (including all previous and later updates and versions). |
| (13) | The latest version is recommended. |
| (14) | Make sure to provide at least 2 virtual CPU cores for each virtual machine |
| (15) | Make sure to have at least 2 CPU cores. |
| (16) | This will be installed automatically during Contact Expert installation. |
| (17) | If Scripting is required, then the x64 architecture is mandatory for the .NET platform – therefore this needs 64-bit OS on the Agent PC. |
| (18) | It is a single package which includes both the .NET Core 6 Runtime and the ASP.NET Core 6 module for IIS. You can run dotnet --list-runtimes to check the exact versions you already have installed. |
Note
When you deploy CE server components onto a computer already having UCMA 5.0 software pre-installed, please make sure the following package is installed as well:
Microsoft Visual C++ 2013 Redistributable (x64) - 12.0.21005
The UCMA 5.0 components CE is using needs this package, while other UCMA 5.0 installers might not have deployed it. If this item is missing, the whole UCMA 5.0 package needs to be re-installed from the CE installer media. This involves uninstalling the previously deployed UCMA 5.0 component and then re-installing it, including the above C++ redistributable package.
Note
You need to repair your existing Microsoft ASP.NET Core Hosting Bundle 6 installation whenever you face a situation where IIS does not start up ASP.NET Core 6 web applications (e.g. AuthenticationSVC). To do the repair you just need to run the same version of Microsoft ASP.NET Core Hosting Bundle installer again by selecting the Repair option now.
Establishing Baseline Environment Capacity
It is not possible for Geomant to foresee real performance capabilities of every possible environment mix. Therefore, in order to establish whether the designated software and hardware environment is going to be optimal for the planned Contact Expert operations, please make sure these prerequisite figures are always available for the CE software components.
In case you plan to co-host 3rd party software to any CE server or agent computer, you are quite likely to have to increase the capacity figures.
Tip
As a generic rule of thumb, the capacity demand should never exceed the upper limit of 70% for any hardware resource (CPU, RAM or storage space) on any CE computer on a sustained manner during business operation.
Applying Required Windows Roles and Features for CE Core Host
The following PowerShell cmdlet applies all Windows Server Roles and Features for the CE server components (Core and/or Recorder). Running this cmdlet is optional, but advised. You can add the required Windows Server Roles and Features manually, individually as well.
After running the cmdlet, a computer restart might be required to complete the installation.
Windows Server 2016 (and newer) operating systems are supported when using the Desktop Experience edition, which in turn contains the Desktop Experience feature package. In such cases so you need to omit this item from the Powershell cmdlet below.
Import-Module ServerManager
Install-WindowsFeature Web-Server, NET-Framework-Features, NET-Framework-45-Features, Server-Media-Foundation, Desktop-Experience, PowerShellRoot, WoW64-Support -IncludeAllSubFeature
To verify that all required items were successfully installed, run the following cmdlet:
Get-WindowsFeature
Corporate Network Firewall Requirements
[CE 6.0 +] As the chat functionality is provided using Geomant's could services, customers wishing to use the chat media will need to expand their corporate firewall rules. The chat media network traffic is using the amqp data protocol which requires one of two network ports to be opened so that Contact Expert servers can access our Cloud Services via the corporate firewall. Which of these is selected depends on the customers' choice:
| Network Target | Transport Type | Port | Network Source |
|---|---|---|---|
| Geomant Cloud Services | Amqp | TCP 5671 | Contact Expert server(s) |
| Geomant Cloud Services | AmqpWebSockets | HTTPS 443 | Contact Expert server(s) |
Note
The agents must also have access to our cloud services using the standard HTTPS protocol.
The following diagram shows the network architecture and connectivity requirements.
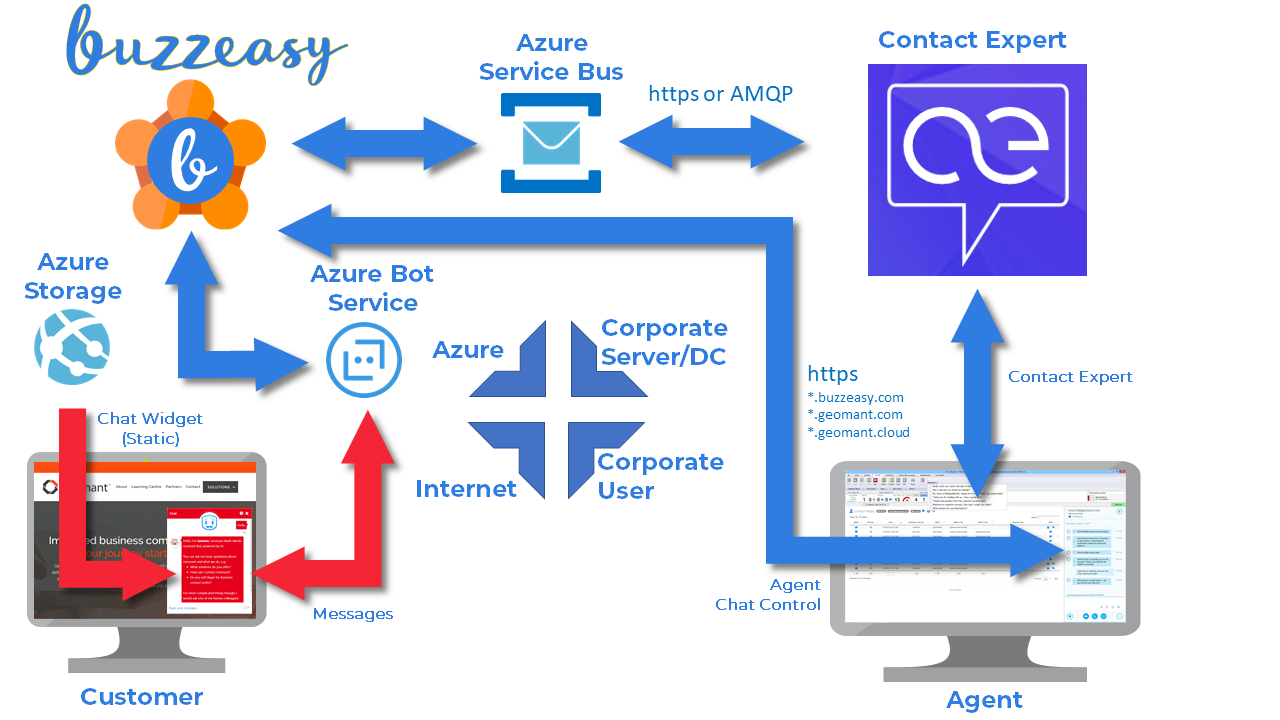
Note
There is no need to open any port for ingress traffic, all communication is initiated towards Geomant cloud services by the CE components on premise.
The list of public FQDNs the on-premises CE components will need access to are:
| FQDN | Protocol | Description |
|---|---|---|
| *.servicebus.windows.net | Amqp or Amqp WebSockets | the generic chat transaction message bus |
| *.buzzeasy.com *.geomant.com *.geomant.cloud |
HTTPS | Geomant cloud APIs and websites the agent computers will need access to |
| *.azurewebsites.net | HTTPS | Cloud based content cache |
It is possible to change these firewall setting after installation, but the configuration of the CE components deployed at the customer premises need to be reviewed and potentially amended with the changes. Please read the WebChat Administration pages in the CE Administration Guide for further details.
Database Prerequisites
Database Login for the Initial Installation
In order to install Contact Expert databases, an sa level user account is required who has the necessary permissions to create:
- Contact Expert databases
- SQL logins to be used by Contact Expert to access its databases
This sa user will execute database scripts to create the needed database objects.
Contact Expert does not require sa user privileges for production operation however. This is merely needed during the installation.
Mixed Authentication Mode
Contact Expert is using SQL Server Authentication to access the databases, so the Mixed Authentication mode feature must be enabled on Microsoft SQL Server (this enables both SQL Server Authentication and Windows Authentication).
TLS v1.2+ Security
CE is compatible with v1.2 or newer TLS security protocols when connecting with the database. It is important to note that both the Microsoft SQL Server running on the CE Database Host as well the Microsoft ODBC driver (32bit) on the CE Core Host(s) must be able to use these TLS protocol versions. For further details read the official document on the TLS 1.2 compatibility of various Microsoft SQL Servers versions.
Note
The Microsoft ODBC Driver might have to be upgraded to more recent versions on older OS versions. See the official ODBC release notes for further details.
SQL Server Management Studio
SQL Server Management Studio software component should be installed on the database host for installation and support purposes later.
SQL Server Instance and Port
Contact Expert can use either the default SQL Server instance or a named instance and it can communicate through any TCP port specified. Also, it is not necessary to specify a fix TCP port for the instance used by Contact Expert as all components can resolve dynamic ports, as well.
(Please note that Contact Expert versions prior to v5.4 require a fix TCP port, unlike the later versions.)
To get more details about the installation of Contact Expert in a named SQL Server instance environment, please read How to install Contact Expert using a named Microsoft SQL Server instance article.
Encrypted connection
These are the pre-requisites in order to encrypt database connections (using TLS) between Contact Expert services and their backend SQL Server instance:
On the Windows Server hosting the SQL Server instance:
Request a valid, trusted certificate as described in this link.
Assign the certificate to the SQL Server instance as described here.
Make sure the service account under which the SQL Server instance is running has permission to read the private key of the certificate.
- On the Windows Server hosting Contact Expert services:
Make sure the root CA certificate exists in the certificate store: Computer Account > Trusted Root Certification Authorities. Import it if it does not exist.
Import the root CA certificate into a Java keystore (optional; e.g. by running [JRE_BIN]\keytool.exe -import C:\xxxx\myRoot-CA.cer -alias myRoot-CA -keystore C:\Geomant\CE\java_sql_cert_store.jks.
After these pre-requisites are satisfied, there are 2 options to start encrypting database connections:
Forcing the encryption of all connections on SQL Server side by setting Force Enctryption = Yes for the SQL Server instance in SQL Server Configuration Manager. In this case, all connections to the SQL Server instance will be encrypted automatically. No encryption option should be enabled/disabled on Contact Expert services side.
Forcing the encryption of Contact Expert database connections on Contact Expert services side: run the following CE Powershell cmdlets:
Set-CESystemDatabaseProperties -EncryptedConnection $true
or
Set-CESystemDatabaseProperties -EncryptedConnection $true -JavaCertificateStorePath '[path]' -JavaCertificateStorePassword '[password]'
and
Set-CEReportDatabaseProperties -EncryptedConnection $true
or
Set-CEReportDatabaseProperties -EncryptedConnection $true -JavaCertificateStorePath '[path]' -JavaCertificateStorePassword '[password]'
In this case, Contact Expert services will establish encrypted connections to the SQL Server instance. Only database connections from Contact Expert services will be encrypted. Other, 3rd party services can still establish unencrypted to the SQL Server instance.
In order to validate that database connections between Contact Expert services and the SQL service instance are encrypted, you can connect to the SQL Server instance using SQL Server Management Studio and run the following query:
Use Master
GO
SELECT client_net_address, encrypt_option FROM sys.dm_exec_connections where client_net_address = '[CE Server IP address]'
GO
Database High Availability Solutions
AlwaysOn Availability Groups
Contact Expert is compatible with SQL Server AlwaysOn Availability Groups features relying on Windows Failover Clustering. When setting up SQL AlwaysOn AG, please mind the followings:
- You can either serve both ACESystem and ACEReport from a single WFC cluster (and AG), or have the two served by two separate clusters (and/or AGs). CE connects to the two databases separately.
- You must create a Listener for the AG. If the two DBs are served from separate AGs then you need a Listener for each. CE will connect to its databases via the Listeners. -To make sure CE will always work with the current primary DB replica only (and that nobody else can connect to the secondaries and change data inadvertently), set the replicas to Automatic Failover, Synchronous Commit, and Readable Secondaries set to disabled.
Compatibility tests were performed with SQL Server 2016 Enterprise running on Windows Failover Clusters on Windows Server 2016 Standard. Scenarios tested were:
- Manual failover on the SQL AG level (using Failover Wizard)
- Manual failover on the cluster level
- Automatic failover during SQL Server unavailability
- Automatic failover during cluster node unavailability
Storage Sizing
Database Storage Size
The required disk space in the above table is an approximate value based on our experiences for the implementation scenario detailed in this article. However, your contact centre might easily need significantly different storage size, therefore the proper disk space requirements should be calculated for the particular customer requirements (number of agents, expected call load, etc.) The below rules might help to scale the storage size.
System Database
The storage space requirement for the Contact Expert system database (ACESystem) can be calculated using the following formula:
100 KB x [number of campaigns] + 4 KB x [number of contact records] + 1 KB x [number of interactions]
Where number of interactions is the total number of voice call, chat and email communication sessions expected to be performed within a given period of time. This storage space is only required until the campaigns and contacts are removed from the system database.
System database storage space calculation example
Assuming an outbound call scenario of 100 campaigns, 10,000 contact records in each campaign and a maximum of 5 dial attempts per contact, the system database requires 100*100 + 4*100*10000 + 1*100*10000*5 ≈ 9 GB of storage space in the file system.
Reporting Database
The storage space requirement for the Contact Expert reporting database (ACEReport) can be calculated using the following formula:
5 KB x [number of interactions]
Where number of interactions is the total number of voice call, chat and email communication sessions expected to be performed within a given period of time.
Reporting database storage space calculation example
Assuming an outbound call scenario of 100 campaigns, 10,000 contact records in each campaign and a maximum 1of 5 dial attempts per contact, the reporting database requires 5 x 100 x 10000 x 5 ≈ 25 GB of storage space in the file system.
Please note that this storage space is required even after these campaign and contact records were removed from the system database.
Accumulating historical data is one of the main goals of the reporting database. However, this also means that an operational maintenance oversight is necessary on a continuous basis to monitor storage use, perform and verify integrity checks, data archival and purging, etc.
Recording Storage Size
If the call recording feature is enabled, Contact Expert stores the recorded voice conversations as individual audio files in the file system. While the required database storage space depends on various parameters explained above, the recording storage size is a function of not only these parameters, but other additional properties like the selected codec, audio file format, etc. which determine the file sizes. Therefore the correct and careful storage size calculation is especially important here.
Please note that the following formula is based on several assumptions e.g. codec, file format, average call length, call frequency etc. Any change in these parameters might cause non-linear changes to the overall storage space requirement.
Using the default Microsoft real time audio codec (RTAudio) and WMA media file format, assuming 90 seconds average talking time and 110 calls per agent per day, the required storage size is:
~ 25 MB / agent / day
Assuming 250 workdays per year and 60 human agents, the annual storage space requirement for Contact Expert Recording service is:
~ 375 GB / year
Storage Technology Compatibility
Contact Expert Recording service is compatible with any storage technology as long as the file system provided to store the recordings appears to be a local NTFS volume for Contact Expert Recording service.
Contact Expert Recording service is compatible with RAID technology. The preferred level is RAID 1.
Provisioning WebChat Cloud Resources from Geomant
CE WebChat media channel is served from Geomant's cloud services. Please refer to your Geomant Representative or Business Partner so the cloud based resources are provisioned in time for your CE deployment schedule.
Preparing the FreePBX Environment
The following steps require strong administrative skills both in Linux and Asterisk platforms.
Preparing the Asterisk REST Interface (ARI) Connection
Contact Expert Voice Gateway connects to Asterisk PBX using the Asterisk REST Interface (ARI). The following steps are required to configure the ARI connection:
- Enable Asterisk Builtin mini-HTTP server.
- Enable Asterisk REST Interface.
- Create a new Asterisk Rest Interface (ARI) user for Contact Expert Voice Gateway (e.g.
ce01user). Ensure the user has authorization for performing non-read operations. This user will be used by Contact Expert Voice Gateway to connect to Asterisk PBX. - Make sure the Asterisk REST Interface is accessible and the user (
ce01user) is able to connect to it.
Preparing the Trunk
A trunk is required to connect to the PSTN network, handle inbound calls and perform outbound calls. The following steps are required to configure the trunk:
- Create a new SIP trunk (e.g.
trunk01). Use PJSIP driver.- Set the SIP Server Address and SIP Server Port and Transport according to your SIP provider's requirements.
- Set the Context to a context where you can specify the dialplan to route inbound calls to the Contact Expert Voice Gateway.
- Other settings should be set according to your SIP provider's requirements and your needs.
- Make sure the trunk is registered and ready to use.
Note
In order to make an unattended (blind) transfer from Contact Expert, the SIP user agent (UA) set up for the trunk must support unattended (blind) transfer as described in RFC 5589.
Preparing the Dialplan
You need to configure Asterisk dialplan to route inbound calls to the Contact Expert Voice Gateway received on the previously created SIP trunk. Use Stasis dialplan application to hand control of a channel over to Contact Expert. The application name set for the Stasis application must match the application name set in the Contact Expert Voice Gateway configuration. An example for dialplan configuration is shown below. The example hangs up the call with 403 Forbidden response if the Contact Expert Voice Gateway is not available.
exten => _!,1,NoOp()
same => n,Stasis(ce01-app)
same => n,GotoIf($[${STASISSTATUS}=FAILED]?app_not_available:end)
same => n(app_not_available),Verbose(0,The app is not available. Send 403 Forbidden.)
same => n,Hangup(21)
same => n(end),NoOp()
Preparing the Skype for Business Environment
The following steps require strong administrative skills both in Microsoft Windows Server and Microsoft Skype for Business Server platforms.
Please note that some settings (e.g. remote desktop connections, user accounts with local administrator, CSAdministrator and other privileges mentioned later) are required only for remote installation purposes and only during the installation process. All of these can be teared down after 'go-live'.
However, these will have to be re-enabled temporarily from time to time in case of any remote maintenance service is provided to support the system.
Preparing the Skype for Business Domain
Assumptions:
- A working Microsoft Skype for Business environment with VoIP, IM, presence and conference services is already implemented.
- Skype for Business users are able to perform Skype for Business calls to each other internally and can dial public numbers, and external callers are able to dial into the Skype for Business environment using public telephony infrastructure (PSTN).
- At least 2 Skype for Business user accounts were created and an external phone number is dedicated for demonstration purposes. The Skype for Business user accounts will be assigned to Contact Expert operators while the dedicated phone number will be assigned to an inbound CE campaign.
The following business information needs to be collected for the installation to kick off:
- Skype for Business Front End FQDN
- The name of each inbound queue and outbound campaign
- Allocated PSTN DID for each inbound queue
- For every agent:
- AD user account name
- SIP URI
Preparing CE Core Host
Follow the next steps in order to prepare CE Core Host:
- Stop the Windows Firewall service.
- Enable Remote Desktop connections for local administrators.
- Add CE Core Host to an Active Directory domain where Microsoft Skype for Business service is available.
- In order to create and assign a certificate to the CE Core Host, please perform the steps described in Configuring CE Certificates article.
Provisioning CE core services as Skype for Business Trusted applications for a non-redundant environment differs from a HA deployment. The following chapters detail the steps for both methods.
Provisioning CE Core Services as a Skype for Business Trusted Application in a Non-redundant Deployment
You might need to run the Enable-CsTopology cmdlet if you receive a warning while performing the steps listed below.
- Log in to the Skype for Business Front End server with a user account having CSAdministrator privileges. Make sure that Skype for Business Server Management Shell is installed.
- Start Skype for Business Server Management Shell in elevated mode.
Execute the following command:
New-CsTrustedApplicationPool -Identity [CE Core Host FQDN] -Registrar [SfB Front End FQDN] -Site [SfB Site ID]Site: You can list your Skype for Business site IDs using the
Get-CsSitecmdlet.Execute the following command:
New-CsTrustedApplication -ApplicationId ACE -Port 9000 -TrustedApplicationPoolFqdn [CE Core Host FQDN]Execute the following command:
New-CsTrustedApplicationEndpoint -ApplicationId ACE -TrustedApplicationPoolFqdn [CE Core Host FQDN] -SipAddress "sip:[your campaign name]@[your SIP domain]" -DisplayName "CE: [Your Campaign's Display Name]" -LineURI "tel:+[campaign line URI]"SipAddress: Specify a domain name in the SIP URI to match your Skype for Business environment. This URI will be associated with a campaign endpoint while configuring CE.
DisplayName: Specify a meaningful display name since Skype for Business users will see this name in their Skype for Business client.
LineURI: If you want the campaign to be callable from outside (via PSTN), then specify a line URI, as well. Otherwise, leave this property unspecified.
Repeat step 5. to create at least 2 campaign endpoints.
Please make sure Skype for Business policies allowing the setup of audio/video conferences and dialling external PSTN numbers are assigned to Contact Expert queue/campaign endpoints. Contact Expert will not operate if these permissions are not granted to the endpoints.
Provisioning CE Core Services as a Skype for Business Trusted Application in an HA Deployment
Please follow the CE Core Services related portions of the steps outlined in the SfB Server Configuration sections of the Administrator's Guide. These will guide you through this setup by showing you an example.
Preparing CE Recorder Host
It is necessary to perform the steps described in this section only in case a dedicated CE Recorder Host has been set up in your Contact Expert environment. If you are using CE Core Host to run call recording services or you do not need call recording, skip this chapter and continue with Gateway Configuration.
Follow the next steps in order to prepare CE Recorder Host:
- Stop the Windows Firewall service.
- Enable Remote Desktop connections for local administrators.
- Add CE Recorder Host to an Active Directory domain where Microsoft Skype for Business service is available.
- In order to create and assign a certificate to the CE Recorder Host, please perform the steps described in Configuring CE Certificates article.
Provisioning CE Recorder Services as a Skype for Business Trusted Application in a Non-redundant Deployment
You might need to run the Enable-CsTopology cmdlet if you receive a warning while performing the steps listed below.
- Log in to the Skype for Business Front End server with a user account having
CSAdministratorprivileges. Make sure that Skype for Business Server Management Shell is installed. - Start Skype for Business Server Management Shell in elevated mode.
Execute the following command: Skip this step if the CE Recorder services will be installed on the CE Core Host instead of a separate CE Recorder Host.
``` powershell New-CsTrustedApplicationPool -Identity [CE Recorder Host FQDN] -Registrar [SfB Front End FQDN] -Site [SfB Site ID]
**Site**: You can list your Skype for Business site IDs using the `Get-CsSite` cmdlet.Execute the following command:
New-CsTrustedApplication -ApplicationId ACE_Recorder -Port 9100 -TrustedApplicationPoolFqdn [CE Recorder Host FQDN]Execute the following command:
New-CsTrustedApplicationEndpoint -ApplicationId ACE_Recorder -TrustedApplicationPoolFqdn [CE Recorder Host FQDN] -SipAddress "sip:[your recorder name]@[your SIP domain]" -DisplayName "CE: [Your Recorder's Display Name]"SipAddress: Specify a domain name in the SIP URI to match your Skype for Business environment. This URI will be associated with a recorder endpoint while configuring CE.
DisplayName: Specify a meaningful display name since Skype for Business users will see this name in their Skype for Business client.
Repeat the previous step in order to create at least 2 recorder endpoints.
Provisioning CE Recorder Services as a Skype for Business Trusted Application in an HA Deployment
Please follow the CE Recorder Services related portions of the steps outlined in the SfB Server Configuration sections of the Administrator's Guide. These will guide you through this setup by showing you an example.
SIP Trunk Configuration
Skype for Business Server's Media bypass feature is not supported by Contact Expert and Refer support feature is supported only in particular cases. For this reason, these features must be disabled by default.
Follow the below steps in order to ensure the mentioned configuration settings are disabled:
- Log in to the Skype for Business Front End server with a user account having CsAdministrator privileges.
- Open Skype for Business Server Control Panel.
- Click Voice Routing, and then click Trunk Configuration. On the Trunk Configuration tab, double-click the trunk configuration settings to be modified.
- Make sure that Refer support setting is set to None and Enable media bypass setting is unchecked. If not, modify and save the settings as required.
For further information on SIP trunk configuration settings in Skype for Business Server, please visit this Microsoft TechNet article.
Gateway Configuration
E.164 Number Format
Contact Expert uses Microsoft UCMA to manage calls. As such, it requires all phone numbers to be specified in E.164 format.
Converting a phone number to an E.164 conform format is called normalization. For inbound calls, it is mandatory to normalize all numbers at the gateway level, before the call reaches the Skype for Business Mediation server. This requires some kinds of number manipulation in the gateway configuration of choice in the following call directions:
- Destination Number IP → Tel
- Destination Number Tel → IP
- Source Number IP → Tel
- Source Number Tel → IP
- Redirect Number IP → Tel
- Redirect Number Tel → IP
Gateway Logs Showing Correct Call Flow Configuration
The following sample information was generated using an AudioCodes gateway, but any other Skype for Business certified gateway can be used.
Source Tel→IP format manipulation
23d:9h:44m:35s (lgr_num)(8244809) PhoneNumber::RemovePrefix - Number change from 00447875635246 to 447875635246 [Time:9:44:35]
23d:9h:44m:35s (lgr_num)(8244810) PhoneNumber::AddPrefix - Number change from 447875635246 to +447875635246 [Time:09:44:35]
The call reaches the SfB Mediation Server in E.164 format
23d:9h:44m:35s INVITE sip:+3618801960@10.168.3.120 SIP/2.0
Via: SIP/2.0/TCP 10.168.0.93;branch=z9hG4bKac783144827;aliasMax-Forwards: 70
From: \<sip:+447875635246@10.168.0.93\>;tag=1c783131289
To:\<sip:+3618801960@10.168.3.120\>
Call-ID: 783130316239201194435@10.168.0.93
CSeq: 1 INVITE
Contact: \<sip:+447875635246@10.168.0.93:5060;transport=tcp\>
Supported: em,100rel,timer,replaces,path,histinfo,resource-priority,sdp-anat
Allow: REGISTER,OPTIONS,INVITE,ACK,CANCEL,BYE,NOTIFY,PRACK,REFER,INFO,SUBSCRIBE,UPDATE
Remote-Party-ID: \<sip:+447875635246@10.168.3.120\>;party=calling;privacy=off;screen=no;screen-ind=0;npi=1;ton=1
Remote-Party-ID: \<sip:+3618801960@10.168.3.120\>;party=called;npi=0;ton=0
User-Agent: Audiocodes-Sip-Gateway-Mediant 1000/v.6.00A.040.005
History-Info: \<sip:+3618801960@10.168.3.120\>;index=1
Content-Type: application/sdp
Content-Length: 229
...
23d:9h:44m:35s SIP/2.0 100 Trying
FROM: \<sip:+447875635246@10.168.0.93\>;tag=1c783131289
TO: \<sip:+3618801960@10.168.3.120\>
CSEQ: 1 INVITE
CALL-ID: 783130316239201194435@10.168.0.93
VIA: SIP/2.0/TCP 10.168.0.93;branch=z9hG4bKac783144827;alias
CONTENT-LENGTH: 0
...
23d:9h:44m:35s SIP/2.0 183 Session Progress
FROM: \<sip:+447875635246@10.168.0.93\>;tag=1c783131289
TO: \<sip:+3618801960@10.168.3.120\>;tag=6225163797;epid=D26BAA6A40
CSEQ: 1 INVITE
CALL-ID: 783130316239201194435@10.168.0.93
VIA: SIP/2.0/TCP 10.168.0.93;branch=z9hG4bKac783144827;alias
CONTACT: \<sip:LYNC.msvoip.dev:5068;transport=Tcp;maddr=10.168.3.120\>
CONTENT-LENGTH: 255
CONTENT-TYPE: application/sdp
ALLOW: CANCELALLOW: BYE
ALLOW: UPDATEALLOW: PRACKREQUIRE: 100relSERVER: RTCC/4.0.0.0
MediationServerRseq: 1
Other Requirements
Recommended Audio File Format
| File format / codec | WMA |
| Channels | 1 (mono) |
| Sample rate | 16 KHz |
| Sample size | 16 bit |
| Encoding bit rate | 16 Kbps |
| Maximum file size | 4 MB |
Music on Hold
Contact Expert provides music-on-hold – and other similar – audio content playing functionality, but does not provide any licensed audio content.
Providing a licensed music (or any other audio content) compliant with local regulations and international copyright laws is the responsibility of the end customer.
Network Adapter Settings
NetBIOS must be enabled on the network adapter(s) used by Contact Expert on each CE Core Host and CE Recorder Host.
If NetBIOS is not enabled, Contact Expert cannot verify that the provided license is valid which results in runtime errors.
Antivirus and Firewall Rules
If there is any antivirus software installed on the CE Core Host and/or the CE Recorder Host, the following folders must be added to the exclusion list in order to disable file system inspections and to prevent the antivirus from blocking the correct operation of Contact Expert:
- [CE install folder] (the path is C:\Geomant\CE by default)
- [CE recording folder] (the path is C:\Media by default)
During the install process, a PowerShell cmdlet is required to be run which will add Configuring CE Firewall Policies to the Windows Firewall. These rules must be kept and the antivirus must not block any network connection from and to Contact Expert.
Please be warned that Contact Expert will not operate properly if the environment does not comply with these rules.